Reading AnonSec’s account of the hack in it’s self-published zine “OpNASADrones”, one can’t help but feel bewilderment at how easily they were able to steal NASA’s files. Indeed, members of the group brag about how effortlessly they breached NASA security, with some even describing an attempt by them to crash one of the drones the agency operates into the Pacific Ocean.
“The Hack
After purchasing an “initial foothold” from a hacker with knowledge of NASA servers over two years ago, the group says it began testing how many machines it could “break into” and “root” – a term referring to an account with complete control over a computer or network.
Brute forcing an administrator’s SSH password, which reportedly only took ‘0.32’ seconds due to the credentials being left as default, AnonSec gained further access inside – allowing them to grab even more login data with a hidden packet sniffer (tcpdump).
The hackers say while some members mapped the network, others analyzed the ‘different missions, airbases and aircraft’ listed by the agency. Public missions like ‘OIB – Operation Ice Bridge’ and drones such as the ‘Global Hawk’ were among those mentioned.
Deleting records of their presence as they hacked deeper into the agency’s system, AnonSec, who even hacked security cameras and uncovered the schematics to one base’s camera layout, then infiltrated the networks at ‘Glenn Research Center, Goddard Space Flight Center and Dryden Flight Research Center.’
Once inside, the group says it began noticing numerous systems and networked devices ‘popping up in scans that were not previously visible…’
After sniffing a password belonging to the system administrator, the hackers say they were eventually able to gain full root access to three network-attached storage (NAS) devices tasked with compiling backups of aircraft flight logs.
‘Now we had all 3 NAS devices automatically making copies of the logs as they are uploaded from the drones and renaming them to look like semi ordinary index files,’ the group writes, mocking the system administrator responsible for protecting the data.
Hackers Attempt to Crash Drone into Pacific Ocean
As the information began flowing unsuspectingly to an AnonSec-controlled server outside of the NASA network, analysis of the data yielded what the hackers described as “weird traffic.”
According to the group, the traffic consisted of ‘pre-planned route option’ files which allow NASA to upload specific flight paths prior to take off.
After protest from several hackers, the group says it decided to carry out a man-in-the-middle (MiTM) attack several months later that replaced the drone route file with one of their own in an attempt to crash the aircraft into the ocean.
‘Several members were in disagreement on this because if it worked, we would be labeled terrorists for possibly crashing a $222.7 million US Drone… but we continued anyways lol,’ the zine states.
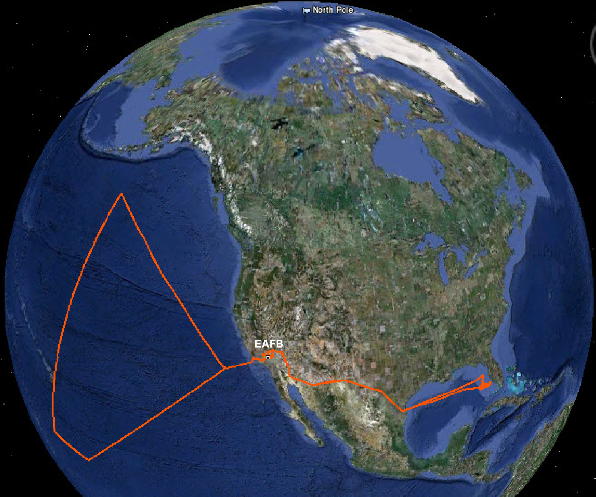
A screenshot from the hackers shows their intended flight path, which they say was cut short after drone pilots on the ground likely noticed the aircraft’s unusual behavior, forcing NASA to restore manual control.
‘This recreated flight is from our attempt to crash the GlobalHawk [sic] into the Pacific Ocean but seemed to have been taken off of the malicious pre-planned route and was controlled via SatCom [sic] by a pilot once GroundControl [sic] realized,’ the hackers write.
Soon after the alleged drone episode, the group says it was completely shut out from NASA’s networks.
‘Whether it was the high amount of traffic sending drone logs across their compromised network or the attempted crashing of a GlowbalHawk [sic] that caused them to FINALLY inspect their networks, we don’t know. But it went down for a while soon after.’
‘When they came back up several days later, we had completely lost access.’
Despite NASA’s ability to boot the hackers by changing passwords and patching critical vulnerabilities, vast amounts of information had already been exfiltrated.
‘People might find this lack of security surprising but its [sic] pretty standard from our experience,’ the group says. ‘Once you get past the main lines of defense, its [sic] pretty much smooth sailing propagating through a network as long as you can maintain access.’
Aircraft Footage & Flight Logs
The 631 videos siphoned out, filmed during 2012 and 2013, feature footage of weather radar readings as well as both manned and unmanned aircraft in multiple stages of flight.
One 59-minute video from May of 2012 shows one such drone taking off from a NASA runway before cutting out 30 minutes into its mission.
Other videos appear to be above large bodies of ice, likely related to the agency’s climate studies.
Flight logs which seem to coincide with some of the video files include the location of take off, aircraft model, mission name, sensor readings and GPS coordinates.
A screenshot showing a small portion of one log file, possibly from 2014, details the flight of a DC-8 involved in the public ‘Alternative-Fuel Effects on Contrails and Cruise EmiSSions’ project.”
Source: Infowars
Photo: NASA


these guys need to be taken down, they have NO REASON whatsoever to have any of that info…
these people need to be taken down, they have NO REASON whatsoever for having this info
That’s what happens when we are replaced by foreign workers!
Barry’s Mooslim outreach for NASA
Bite Me.
Why don’t we have people as smart as these hackers and why are we not running them down and shutting them down; with very heavy penalties? The People want to know!
Don’t Drone me Bro!
Or is this a cover for the information that Clinton exposed in her emails?
Don’t ask, just believe.
Intimidation